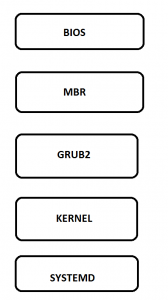
We are going to see how to use sed command in Unix/Linux
SED – Stream Editor This is doing maximum operation over the file like insert, delete, search and replace the word or a character. mostly its used to find and replace operation in Linux/Unix environment.
Note: Once executed sed command, the output will be changed as per your requirement and original file remain the same.
Substituting or replacing string in a file using sed:
Mostly we are using sed to replace the string in a file. Use the below command to change a string. Here I am going to change platform as technology and I will use the below mentioned same file in all the examples.
[root@localhost ~]# cat > sed.txt Linux is more secure and opensource operating system and Linux is low cast. Multiuser is available in Linux and Linux is powerful OS. Linux is the current and future OS in administration.
The command for substituting and replacing string in above file:
[root@localhost ~]# sed `s/Linux/Unix/` sed.txt Unix is more secure and opensource operating system and Linux is low cast. Multiuser is available in Unix and Linux is powerful OS. Unix is the current and future OS in administration.
Command to change the nth occurrence of the string/pattern in a line:
Below command will change the nth string/pattern in line and we are going to change the second string.
[root@localhost ~]# sed 's/Linux/Unix/2' sed.txt Linux is more secure and opensource operating system and Unix is low cast. Multiuser is available in Linux and Unix is powerful OS. Linux is the current and future OS in administration.
Command to change the string/pattern which is matching to our string in a file:
Command will change all the string which matching to our given string/pattern in a file and we need to use g option for this.
[root@localhost ~]# sed 's/Linux/Unix/g' sed.txt Unix is more secure and opensource operating system and Unix is low cast. Multiuser is available in Unix and Unix is powerful OS. Unix is the current and future OS in administration.
Command to change nth occurrence of all the line in a file which matching to our given string/pattern:
This command will change all the nth occurrence in all the lines.
[root@localhost ~]# sed 's/Linux/Unix/2g' sed.txt Linux is more secure and opensource operating system and Unix is low cast. Multiuser is available in Linux and Unix is powerful OS. Linux is the current and future OS in administration.
g is the key to change the occurrence globally in a file and here we are mentioning which occurrence have to be changed in a file which we mentioned as 2.
Command to set parenthesize first letter of all the characters in a line:
[root@localhost ~]# sed 's/\(\b[A-Z]\)/\(\1\)/g' sed.txt (L)inux is more secure and opensource operating system and (L)inux is low cast. (M)ultiuser is available in (L)inux and (L)inux is powerful (O)S. (L)inux is the current and future (O)S in administration.
Here all the capital letters are taken as a first word and parenthesize has been set.
Command to replace the string/pattern in specific line:
[root@localhost ~]# sed '3 s/Linux/Unix/' sed.txt Linux is more secure and opensource operating system and Linux is low cast. Multiuser is available in Linux and Linux is powerful OS. Unix is the current and future OS in administration.
Command to duplicate/print the modified line again:
Below command will print the modified line two times.
[root@localhost ~]# sed 's/Linux/Unix/p' sed.txt Unix is more secure and opensource operating system and Linux is low cast. Unix is more secure and opensource operating system and Linux is low cast. Multiuser is available in Unix and Linux is powerful OS. Multiuser is available in Unix and Linux is powerful OS. Unix is the current and future OS in administration. Unix is the current and future OS in administration.
Command to display/print the modified line alone:
in below example we are going to change the string in second line and will display the second line alone because its modified. We should use -n option along with /p tag in sed command.
[root@localhost ~]# sed -n '2 s/Linux/Unix/p' sed.txt Multiuser is available in Unix and Linux is powerful OS.
Command to replace string/pattern in range of lines:
Command will replace the first occurrence in 2 and 3rd line.
[root@localhost ~]# sed '2,3 s/Linux/Unix/' sed.txt Linux is more secure and opensource operating system and Linux is low cast. Multiuser is available in Unix and Linux is powerful OS. Unix is the current and future OS in administration.
Command to replace all the occurrence in rage of lines:
in below command string will be replaced in 2 and 3rd lines of all occurrence.
[root@localhost ~]# sed '2,$ s/Linux/Unix/g' sed.txt Linux is more secure and opensource operating system and Linux is low cast. Multiuser is available in Unix and Unix is powerful OS. Unix is the current and future OS in administration.