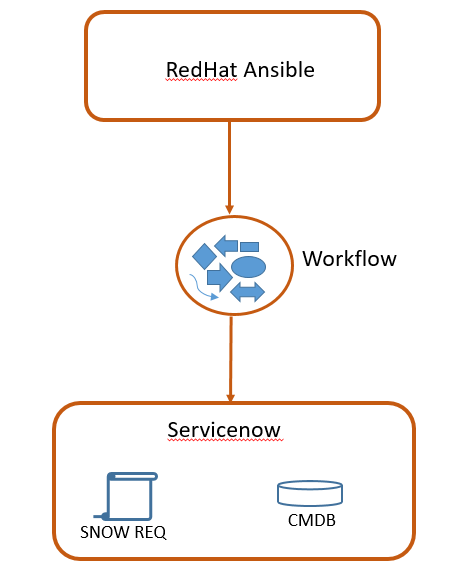
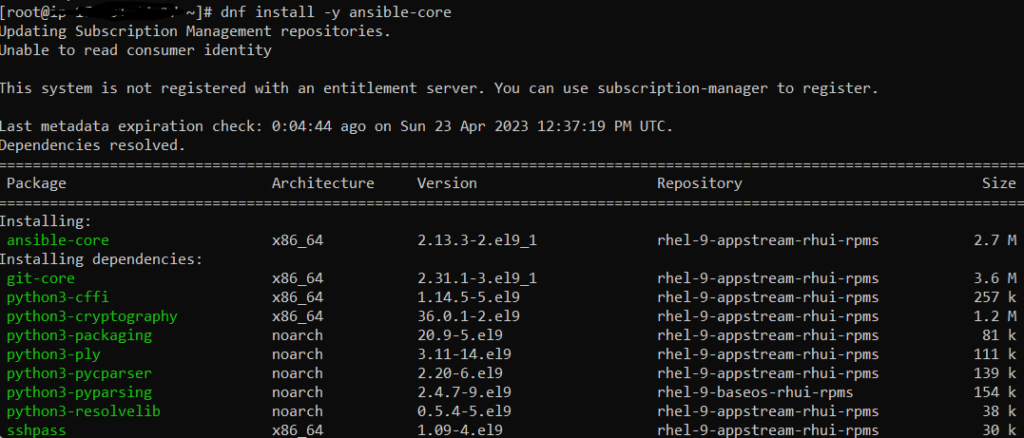
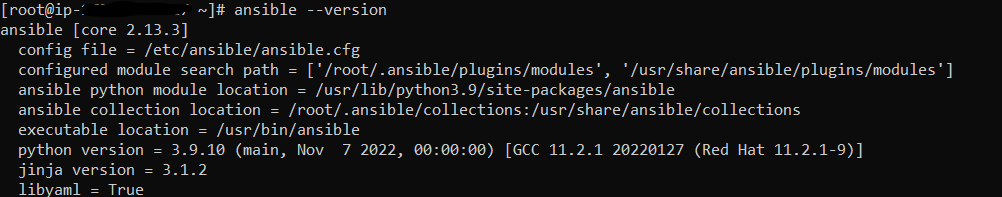
Unreachable Host: port unreachable : port unreachable
I do have access to ssh into the destination machine, and it works, but whenever I run this playbook, I get this error output:
sudo ansible-playbook test.yml PLAY [web] ***************************************************************************************************************************************************************************************** TASK [Gathering Facts] *********************************************************************************************************************************************************************************** fatal: [machine]: UNREACHABLE! => {"changed": false, "msg": "Failed to connect to the host via ssh: Permission denied (publickey,gssapi-keyex,gssapi-with-mic,password,keyboard-interactive).\r\n", "unreachable": true} to retry, use: --limit @/ansible-play/test.retry PLAY RECAP *********************************************************************************************************************************************************************************************** machine : ok=0 changed=0 unreachable=1 failed=0
Solution 1:
Try to check the SSH arguments and I used below, and it helps me sometime.
#ansible-playbook --user=brines -vvv test.yml
Solution 2:
Invalid SSH Configuration also may lead this issue. So, hvae to fix the SSH configuration issue or copy & paste the ssh keys on concern hosts.
#cd /root/.ssh #ssh-keygen -t rsa
save key under the name of id_rsa
#cat id_rsa.pub
copy the entire key and paste in file (of master node located at path: /.ssh/ or /root/.ssh) as:
#vi authorized_keys
Then run this to check:
#ansible all -m ping -u brines
Output should be like this:
master-node | SUCCESS => { "changed": false, "ping": "pong" }